Chain of Harm Methodology
The Chain of Harm is a tested, replicable approach for practitioners to design evidence-based and locally led information integrity programming, with a focus on traditionally marginalized perspectives.
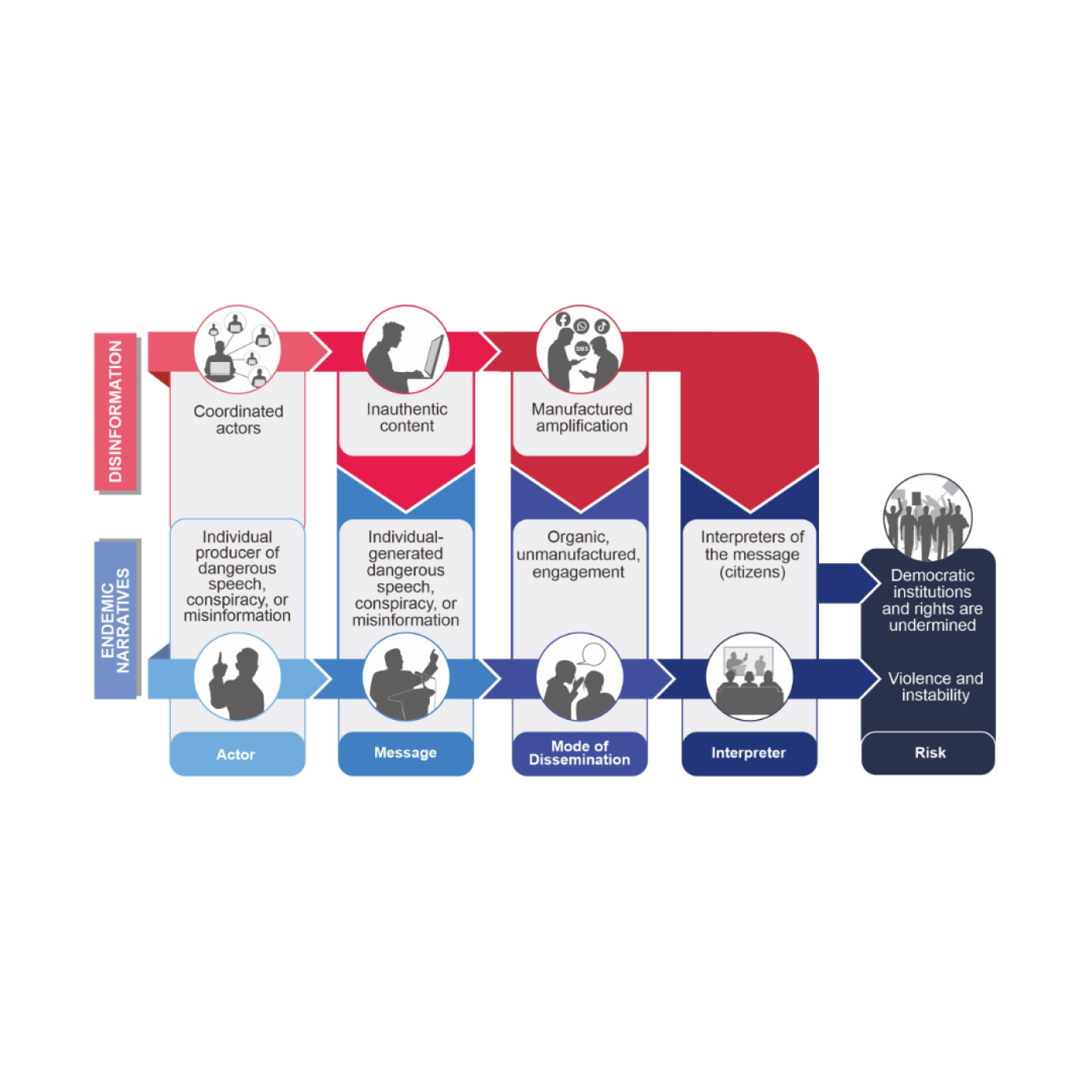
Since IFES published Disinformation Campaigns and Hate Speech: Exploring the Relationship and Programming Interventions in 2019, challenges to public trust, public health and social cohesion presented by inaccurate, inciteful, and deliberately deceptive information have continued to demand innovative responses. The Chain of Harm was introduced in that 2019 publication and conceptually expanded upon in The Chain of Harm: Designing Evidence-based, Locally Led Information Integrity Programming.
The Chain of Harm is a framework that breaks down the challenges of disinformation, misinformation, and dangerous speech (DMDS) into five interrelated stages (actor, message, mode of dissemination, interpreter, and risk). Each stage describes a discrete intervention point to disrupt the ultimate manifestation of harm. This five-stage approach supports the design of multi-layered programming that more effectively promotes healthy information environments around moments of critical social and civic importance, with particular emphasis on designing programming that is responsive to the different experiences of diverse populations.
The Chain of Harm has proven both useful and replicable for the broader community of development practitioners, particularly those who aim to create evidence-based and locally led programming, especially in the following areas:
- Designing more nuanced information integrity programming using the Chain of Harm
The Chain of Harm depicts the interplay of deliberate disinformation campaigns with endemic conspiracy, misinformation, and dangerous speech across the five stages and provides a means for practitioners and researchers to identify multi-layered intervention strategies and focus scarce resources on the most impactful interventions.
- Creating locally led, evidence-based programming through the Chain of Harm Co-design Workshop
The Chain of Harm can be used to create evidence-based, locally led information integrity programming that centers the perspectives of local communities, with a focus on traditionally marginalized or underrepresented populations. Step-by-step implementation guidance for the Co-design Workshop is contained within Chain of Harm Co-Design Workshop: An Implementation Guide for Designing Evidence-Based, Locally Led Information Integrity Programming.
- Culturally responsive evaluation
The Chain of Harm is valuable as a culturally responsive evaluation tool that helps ensure the inclusion of local voices and perspectives in evaluations of information integrity programs.
- Inclusive threat modeling
The Chain of Harm can be used as the foundation for a participatory threat modeling workshop that generates insights about the diverse experiences of underrepresented populations with respect to digital safety and cybersecurity risks. These insights can be used to design and implement more responsive interventions and risk mitigation strategies.





